What is C2C?
The Department of Defense (DoD) faces several cyber security challenges when it comes to ensuring only authorized devices are connected and operating on enterprise networks. Today, many of the DoD services, Combatant Commands and Fourth Estate Services have manual processes in place to determine and report their current Cyber Scores. Even with tools such as ACAS, SCCM, Tanium, and HBSS (or ESS) organizations are still manually sifting through these applications to try and determine, with some level of accuracy, their current cyber hygiene posture.
C2C is part of the DoD-wide mandate to ensure restricted device access from unauthorized users. This includes reducing known vulnerabilities by detecting, identifying, characterizing, and deterring anomalous behaviors to secure configuration of the network and its information resources. The comprehensive cybersecurity framework of tools and technologies included in C2C is designed to increase cybersecurity efficiency across the DoD’s current and emerging operational environments.
The Three Wire Solution
Team Three Wire Systems was put on contract in September of 2018, to deploy the ForeScout Comply-to-Connect (C2C) & Continuous Monitoring (CM) as a Managed Service in support of a United States Air Force (USAF) Network Operations Security (NOS) activity. We also supported the USAF in other efforts such as an assessment of the Forescout C2C solution in preparation for USAF’s move towards DoD compliance for C2C implementation.
Three Wire Forescout Subject Matter Experts (SMEs) will support engineering the software platform, licensing delivery, and operations to help provide the complete situational awareness of the enterprise and the ability to coordinate actions to reduce cybersecurity risk across the DoDIN. In support of the physical infrastructure, which includes IT equipment and corresponding services, the SMEs will help facilitate delivery of C2C policies and administrator support commensurate with the rollout of licensing and implementation of Network Access Control (NAC) software across the DoD. Three Wire operates on a zero trust to replace implicit trust with explicit permission.
Three Wire's C2C Solution includes four vital parts:
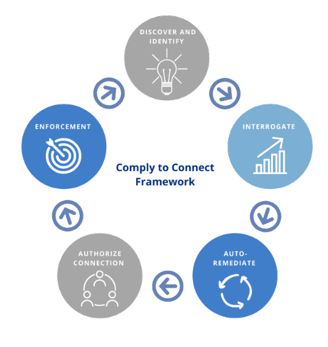
- Comprehensive Network-Based Visibility, Discovery, and Classification of Devices
- Redundant Manageability and Control of Devices
- Orchestration with Mandated Security and Network Management Solutions
- Continuous Monitoring and Automated Remediation
As organizations plan to transition to a more-secure Zero Trust Architecture (ZTA) and Zero Trust Network (ZTN), cybersecurity professionals understand the road to ZTA/ZTN incorporates C2C as a foundational element. Three Wire’s expertise and proven performance in C2C establishes us as an industry leader in Cybersecurity/C2C and as a trusted partner for organizations seeking to implement a Zero Trust Architecture.


